A Classical Introduction to Cryptography - Exercise Book
Welcome to the companion site of the exercise book!
Last modification of this page:
Errata Page for the Exercise Book
This is the errata web page for the book. If you find a mistake that is not already listed here, please report it to
The latest version of the errata can either be consulted on-line (see below) or downloaded as a [ps file] or as a [pdf file].
1 Prehistory of Cryptography
p. 8, Solution 1. In question 4, diagrams (a) and (c) do represent a surjective function.2 Conventional Cryptography
p. 37, Solution 5. In question 1(a), one should read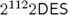 and
and
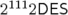 for the
worst-case and the average case repspectively.
for the
worst-case and the average case repspectively.
p. 38, Solution 6. In the second question, the probability that a given plaintext
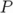 is mapped on a given
ciphertext
is mapped on a given
ciphertext 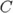 through the
uniformly distributed random permutation
through the
uniformly distributed random permutation
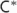 should be
expanded as follows:
should be
expanded as follows:
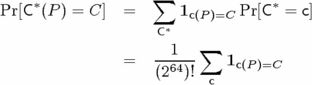
3 Dedicated Conventional Primitives
p. 71, Solution 4. In the third question, one should read “Clearly, they all produce [...]” instead of “Clearly, the all produce [...]”.p. 73, Solution 4. In the eighth question, one should read “with a probability e−λ” instead of “with a probability eλ”.
4 Conventional Security Analysis
p. 86, Exercise 7. The second of the three boolean functions is not used in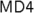 It is actually part of
It is actually part of
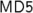 which also uses a fourth function.
which also uses a fourth function.
p. 109, Solution 8. On Figure 4.9, ω−1 is wrong: the inputs should be swapped before the xor.